Load Invisishell first
Then Load PowerView by dot sourcing
1
| . \<path to the script>
|
1
| . C:\AD\Tools\PowerView.ps1
|
Domain Enumeration
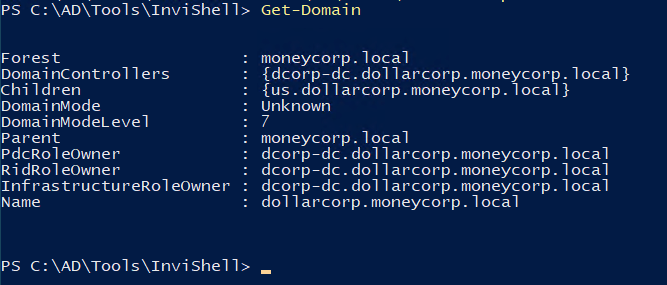
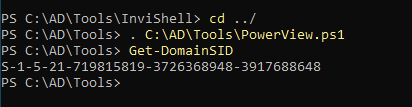
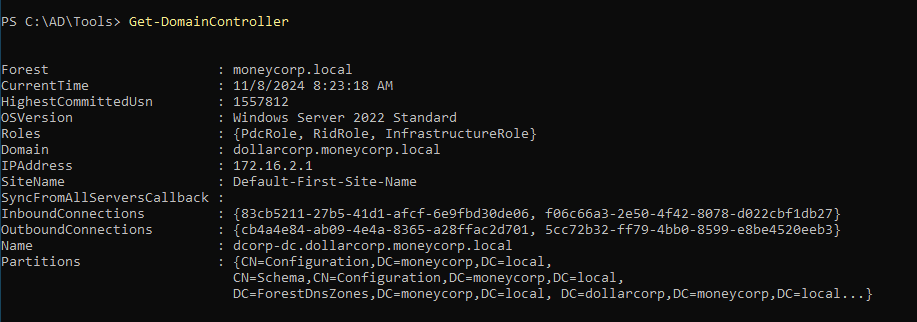
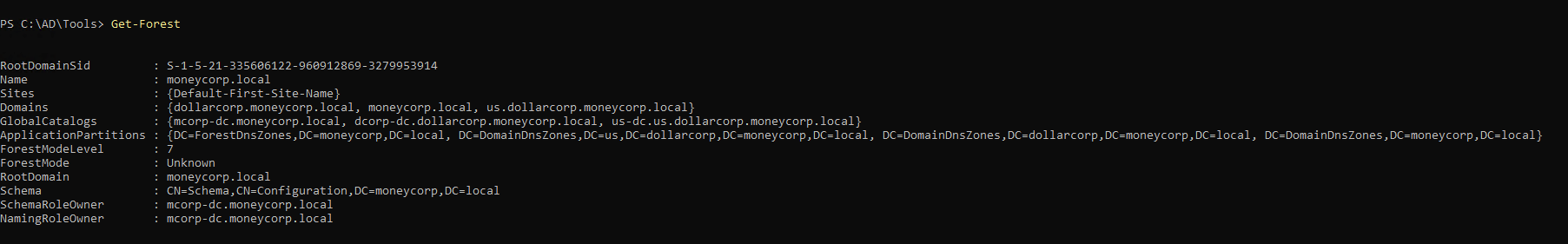
Get domain gives you info about current forest
Forest - moneycorp.local current domain - dollarcopr.moneycorp.local domain controller 1 domainmodelevel 7 - 2016 server
1
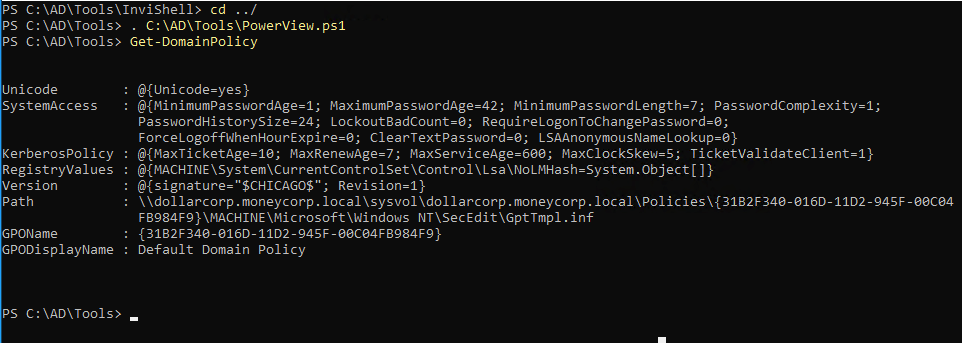
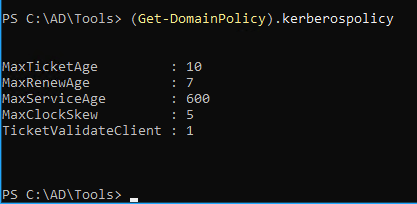
| (Get-DomainPolicy).KerberosPolicy
|
DomainUser Enumeration
To list out the user details
1
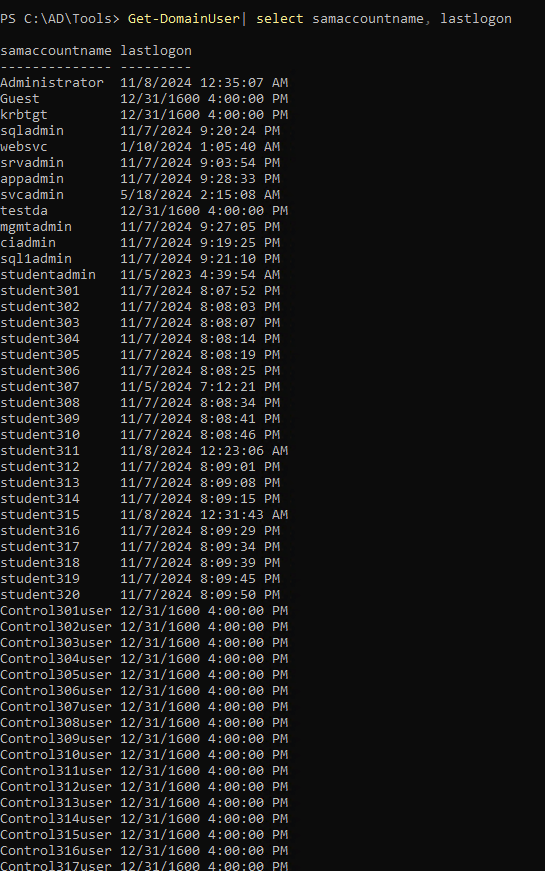
| Get-DomainUser | select samaccountname
|
1
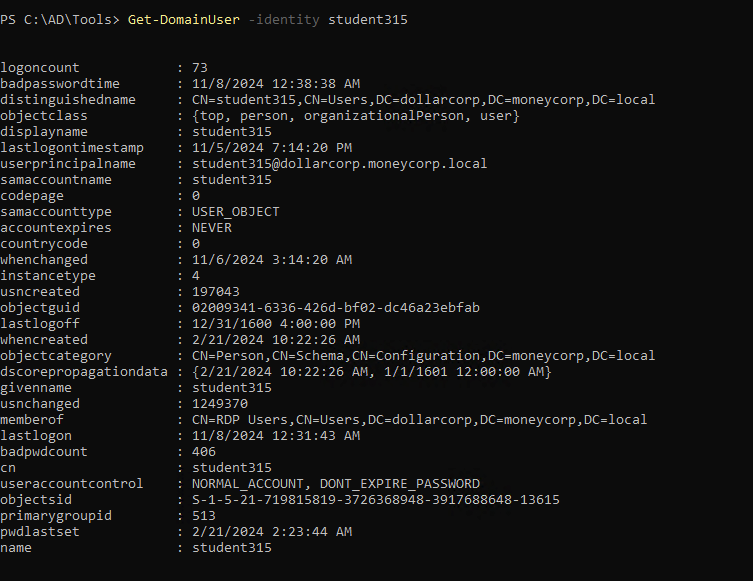
| Get-DomainUser -identity student315
|
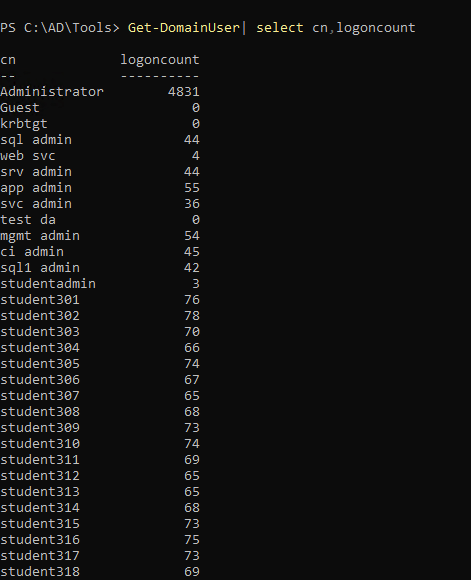
To Find decoy,
1
| Get-DomainUser | select cn, logoncount
|
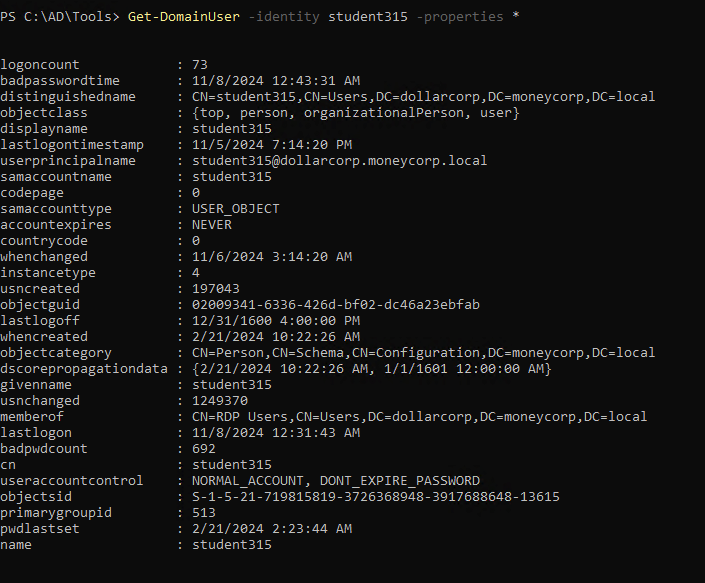
1
| Get-DomainUser -identity student315 -properties *
|
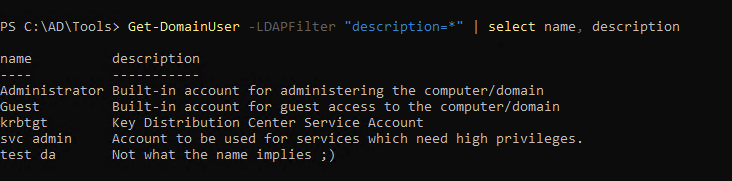
1
| Get-DomainUser -LDAPFilter "description=*" | select name, description
|
DomainComputer Enumeration
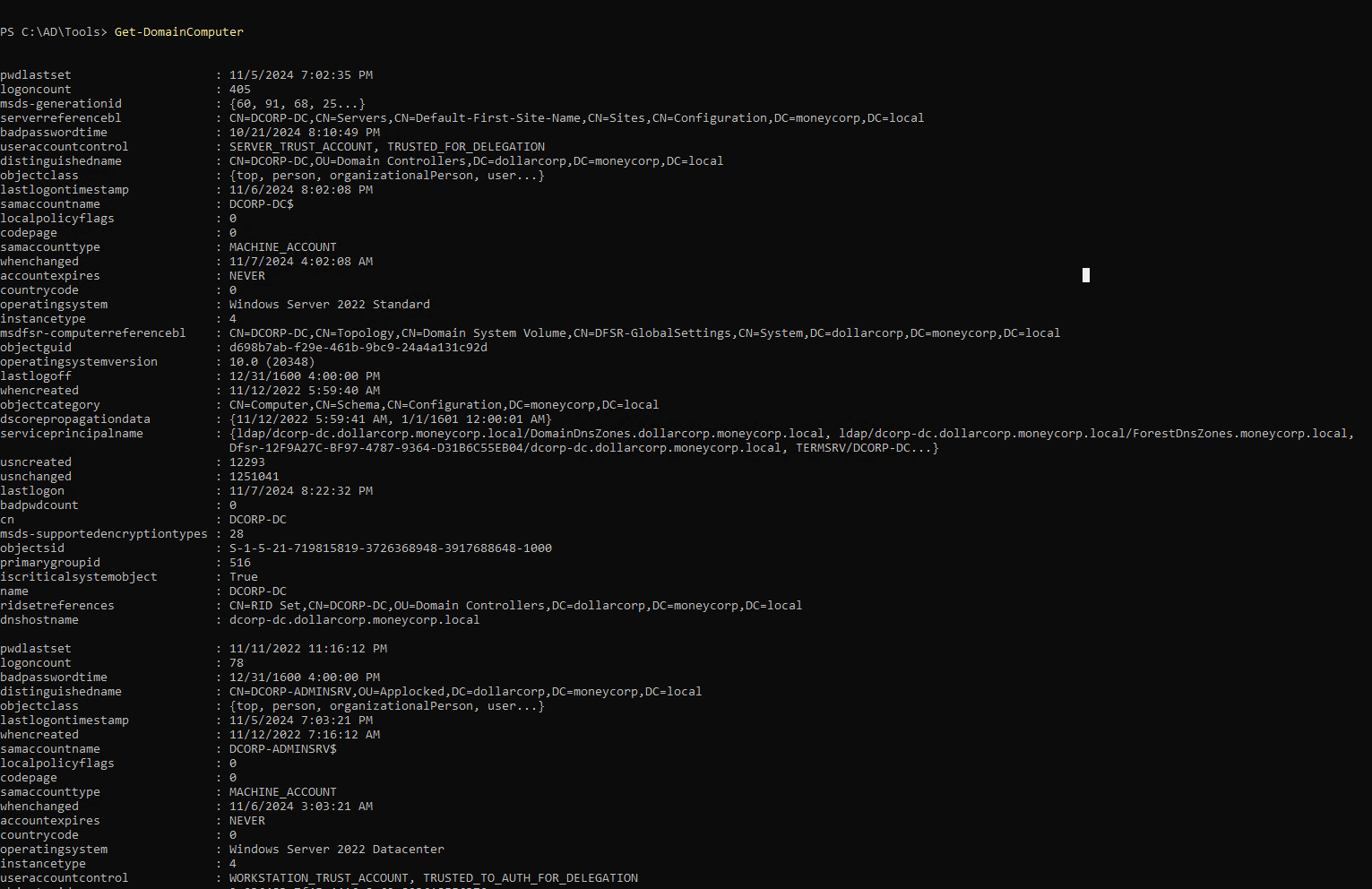
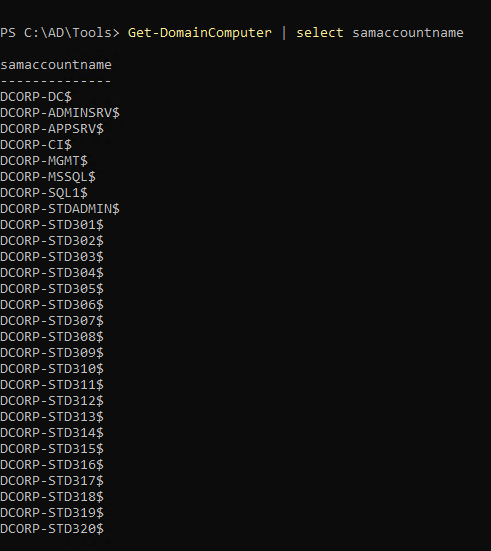
1
| Get-DomainComputer | select samaccountname
|
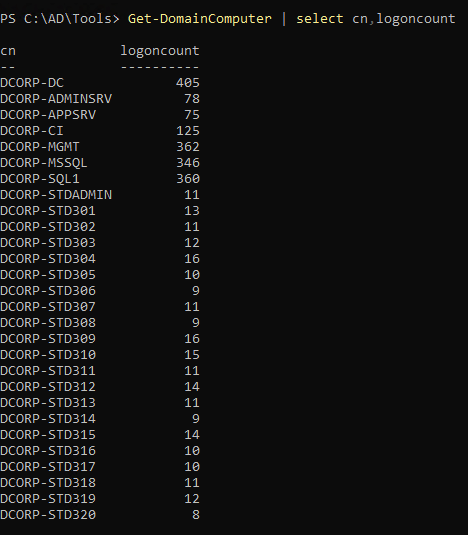
computer object
1
| Get-DomainComputer | select cn,logoncount
|
DomainGroup Enumeration
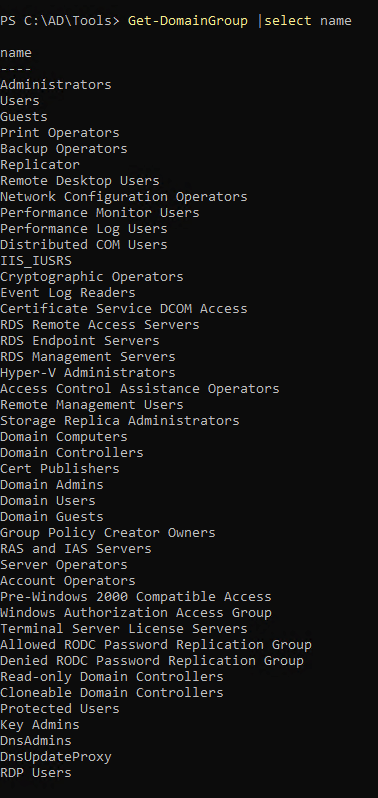
1
| Get-DomainGroup | select name
|
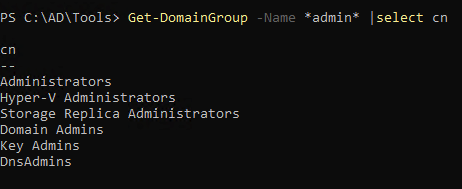
1
| Get-DomainGroup -Name *admin* | select cn
|
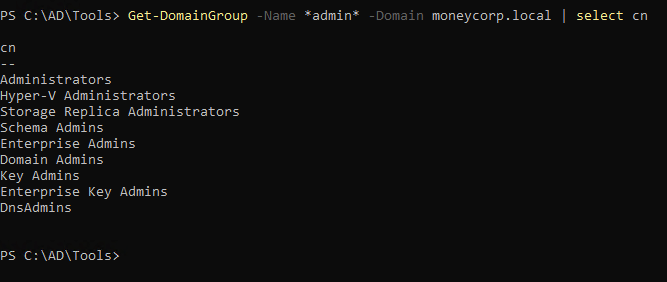
1
| Get-DomainGroup -Name *admin* -Domain moneycorp.local | select cn
|
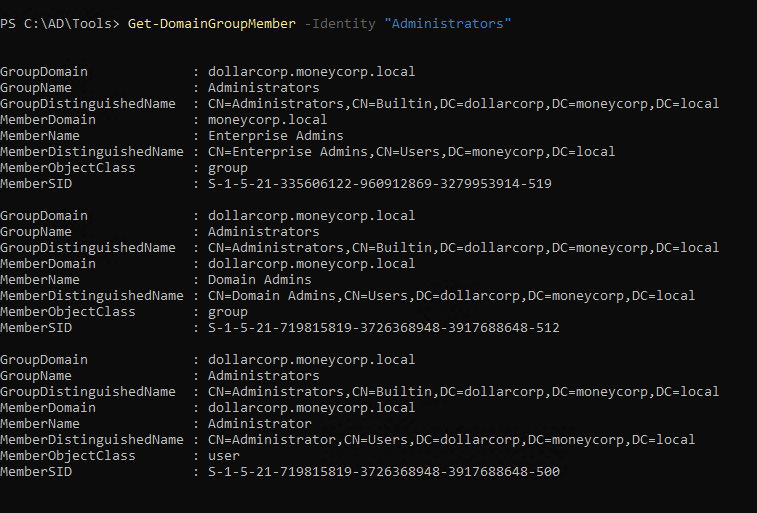
1
| Get-DomainGroupMember -Identity "Administrators"
|
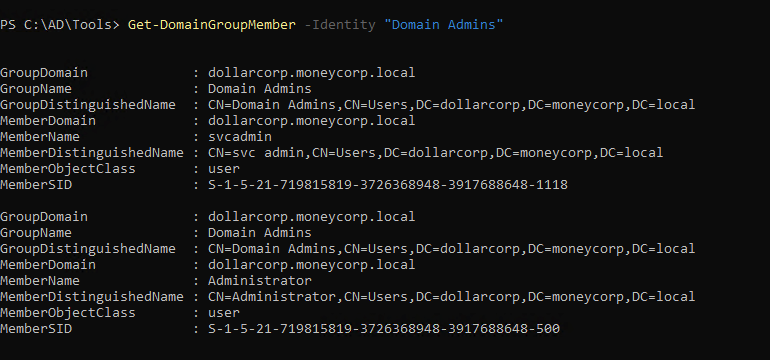
1
| Get-DomainGroupMember -Identity "Domain Admins"
|
sid 500 is default admin account
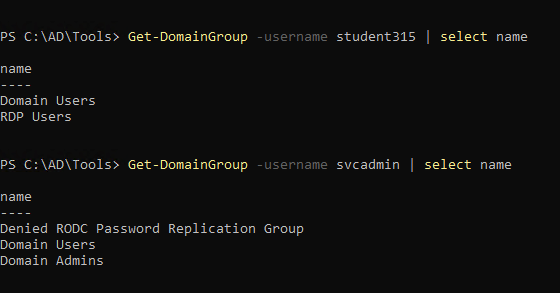
1
| Get-DomainGroup -username student315 | select name
|
LocalGroup Enumeration
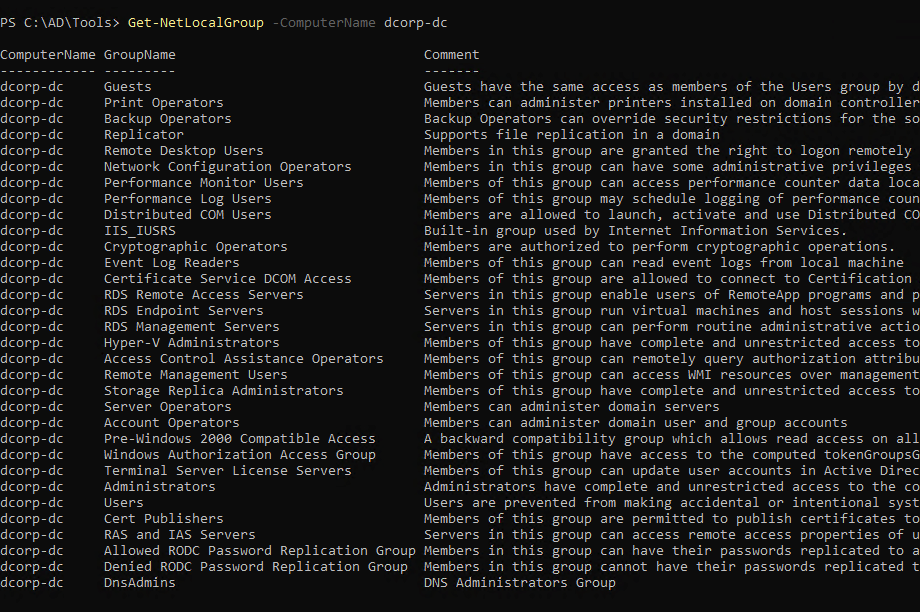
1
| Get-NetLocalGroup -ComputerName dcorp-dc
|
for dc no admin rights required to list out the localgroup in dc, but in member machine need admin rights to list out
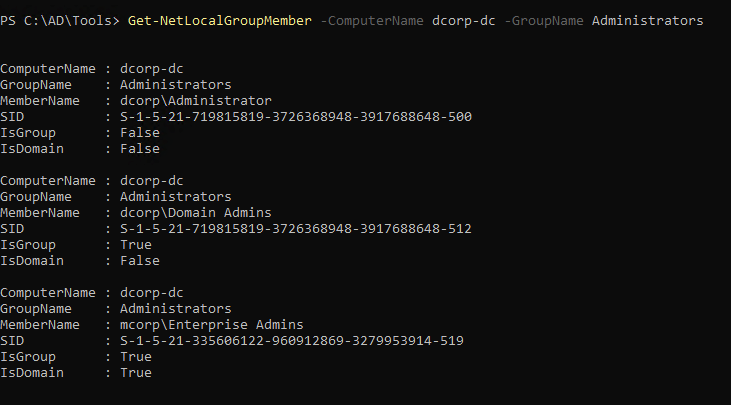
1
| Get-NetLocalGroupMember -ComputerName dcorp-dc -GroupName Administrators
|
Learning Objective 1
1
| Get-DomainGroupMember -name "Enterprise Admins" -domain moneycorp.local
|
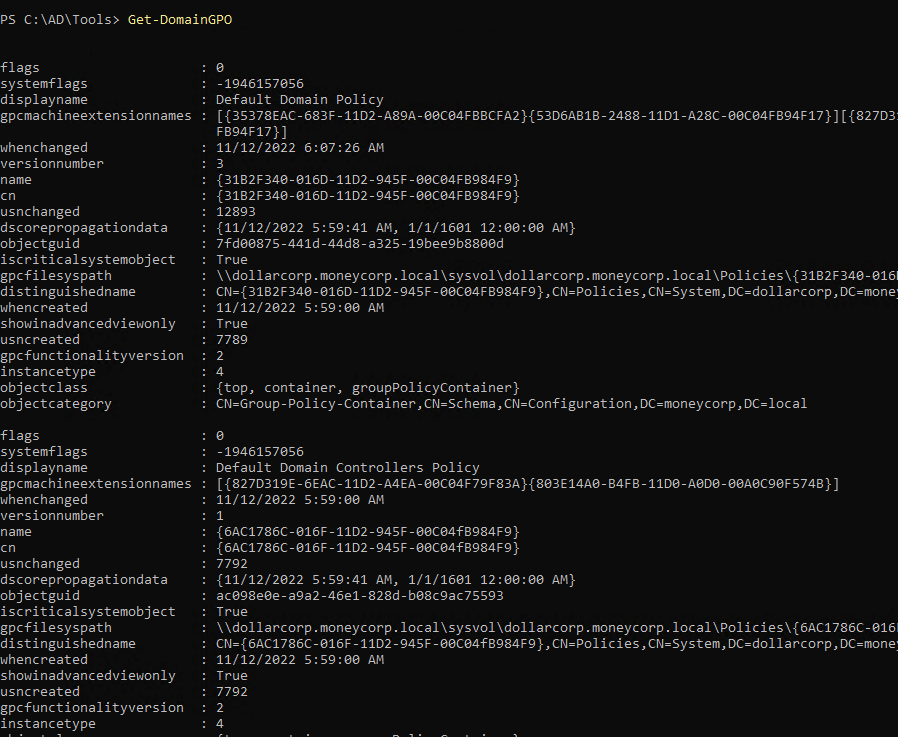
Domain Group Policy Enumeration
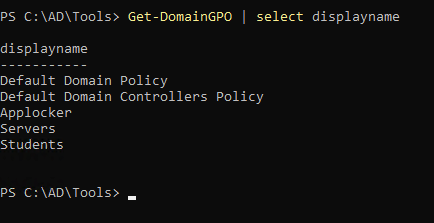
1
| Get-DomainGPO | select displayname
|
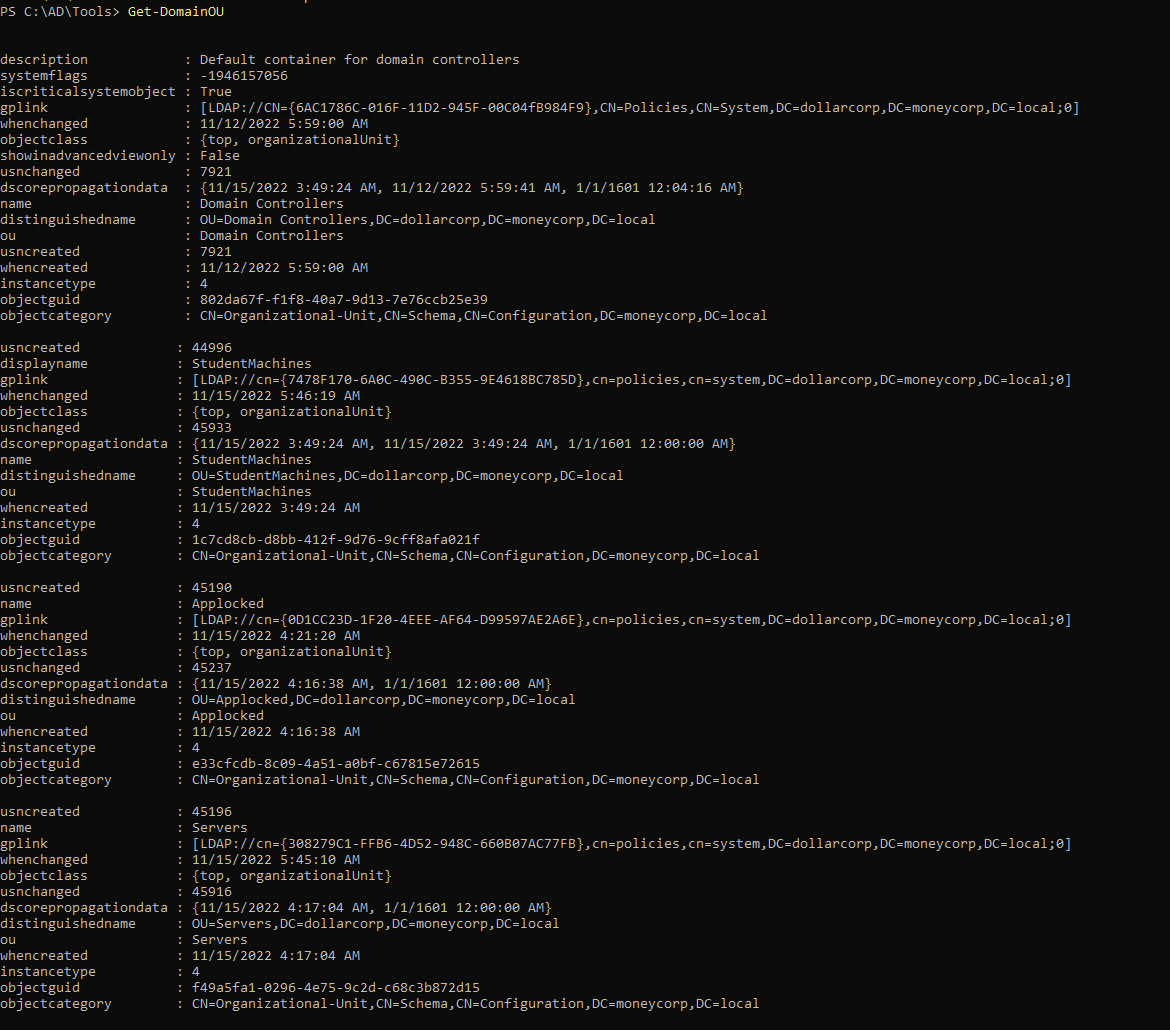
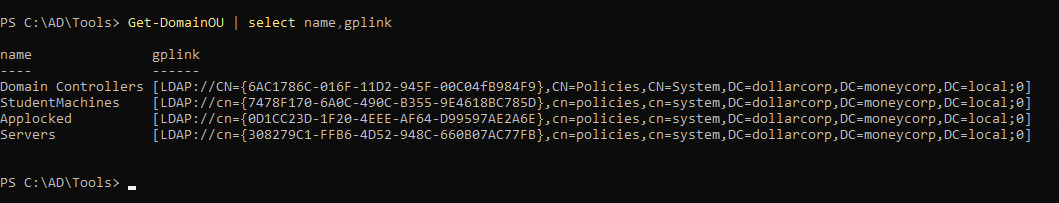
1
| Get-DomainOU | select name,gplink
|
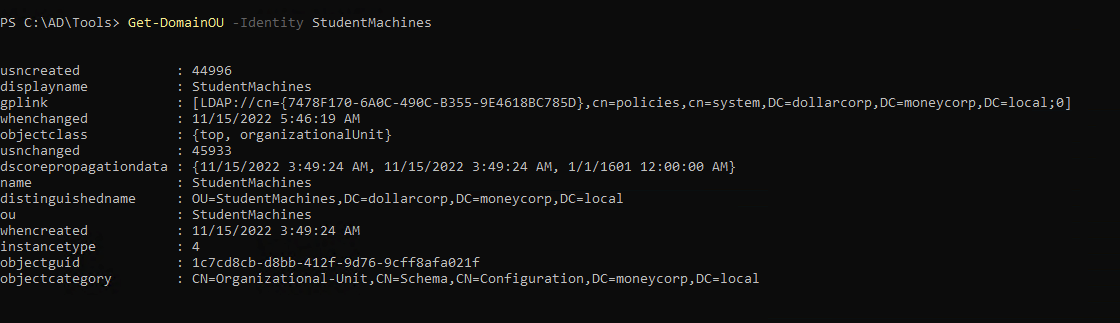
1
| Get-DomainOU -Identity StudentMachines
|
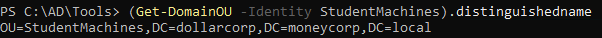
1
| (Get-DomainOU -Identity StudentMachines).distinguishedname
|
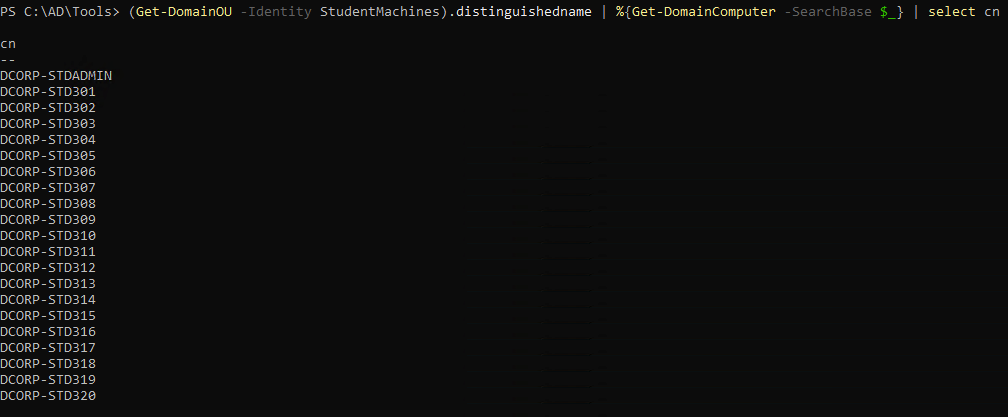
1
| (Get-DomainOU -Identity StudentMachines).distinguishedname | %{Get-DomainComputer -SearchBase $_} | select cn
|
Domain Enumeration - ACL
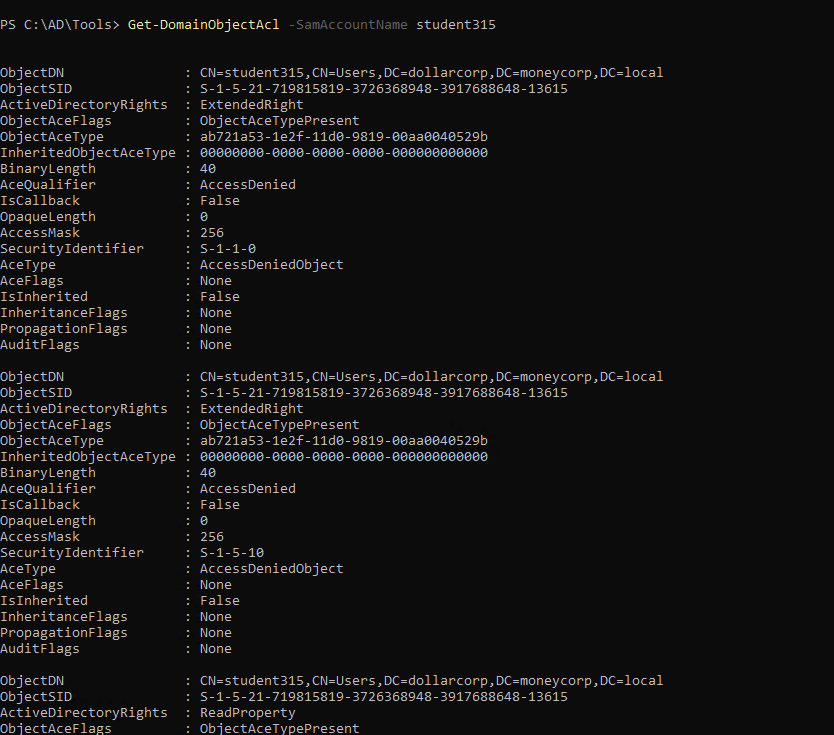
Whenever the process trying wants to access an object, process could have access token (identity & privs of the user) Security Descrtiptors (SID, DACL, SACL)
1
2
| DACL - list of who have permission & what is the permission
SACL - audit success or failure
|
1
| Get-DomainObjectAcl -SamAccountName student315
|
1
| Get-DomainObjectAcl -SamAccountName student315 -ResolveGUIDs
|
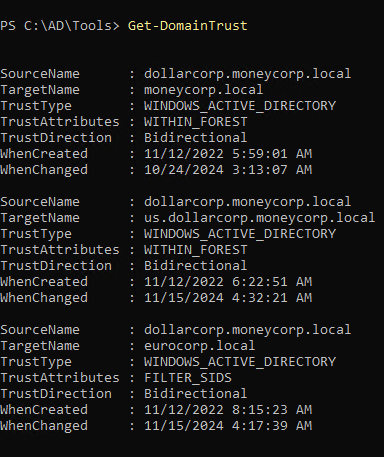
Domain Enumeration Trusts
1
| Get-DomainTrust -Domain eurocorp.local
|
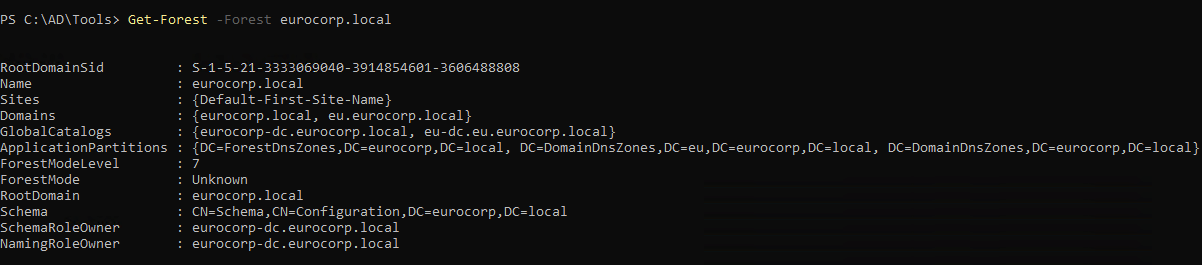
1
| Get-Forest -forest eurocorp.local
|
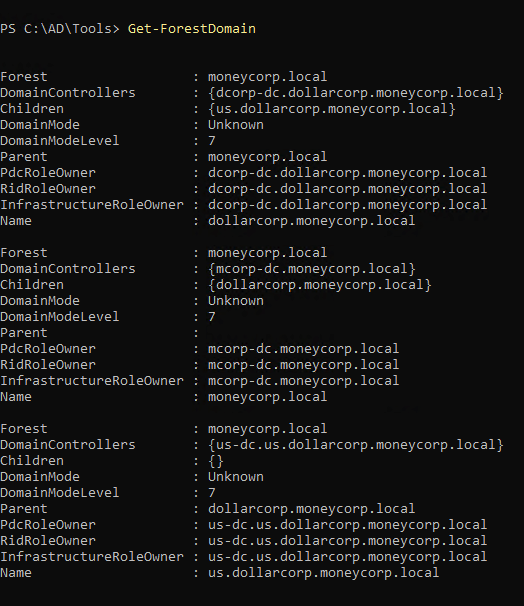
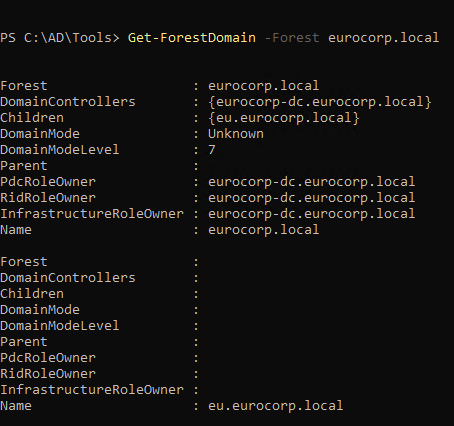
1
| Get-ForestDomain -Forest eurocorp.local
|
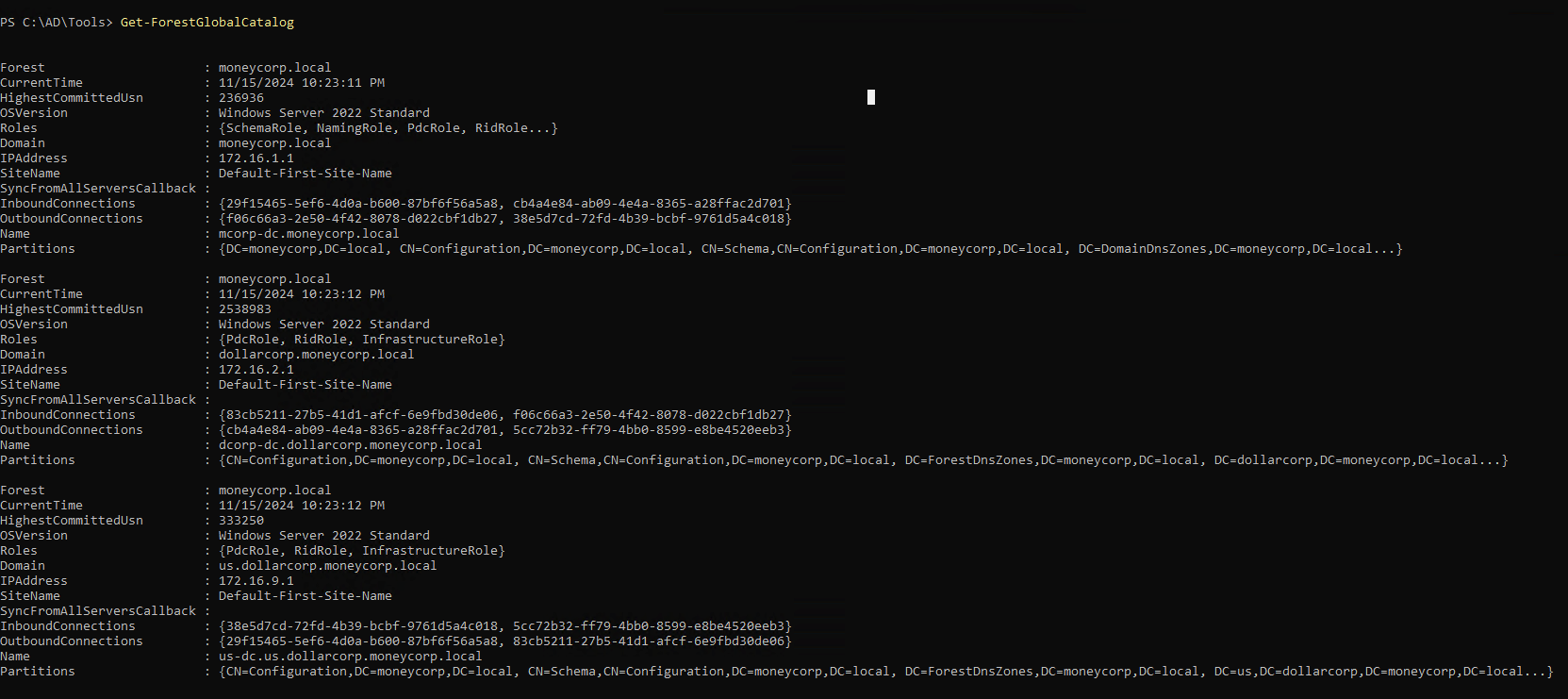
1
| Get-ForestGlobalCatalog
|
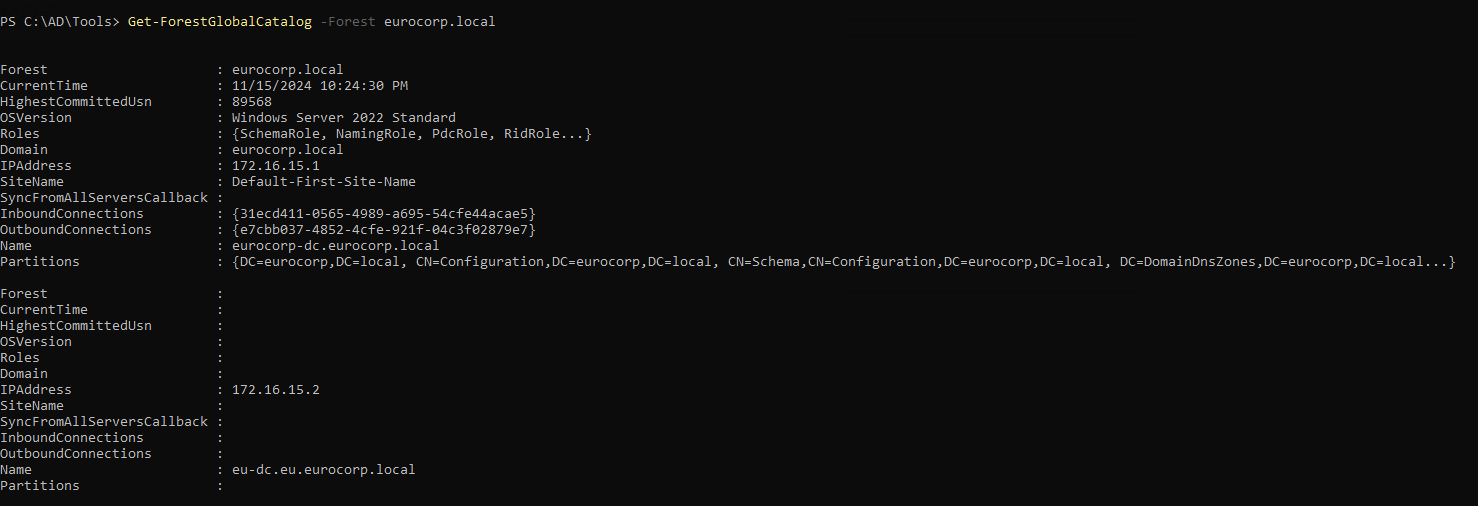
1
| Get-ForestGlobalCatalog -Forest eurocorp.local
|
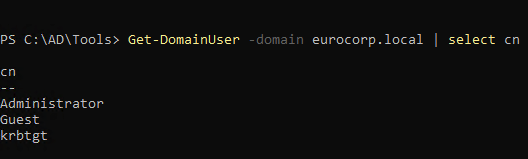
1
| Get-DomainUser -Domain eurocorp.local
|
All enumeration is valid if trusts is there
Domain user Hunting
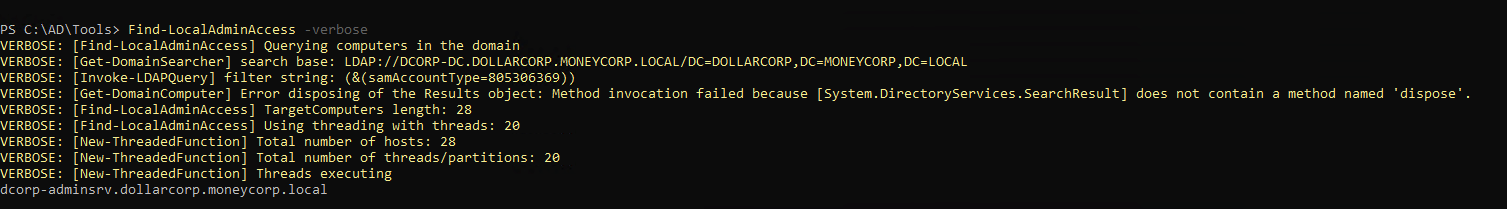
1
| Find-LocalAdminAccess -verbose
|
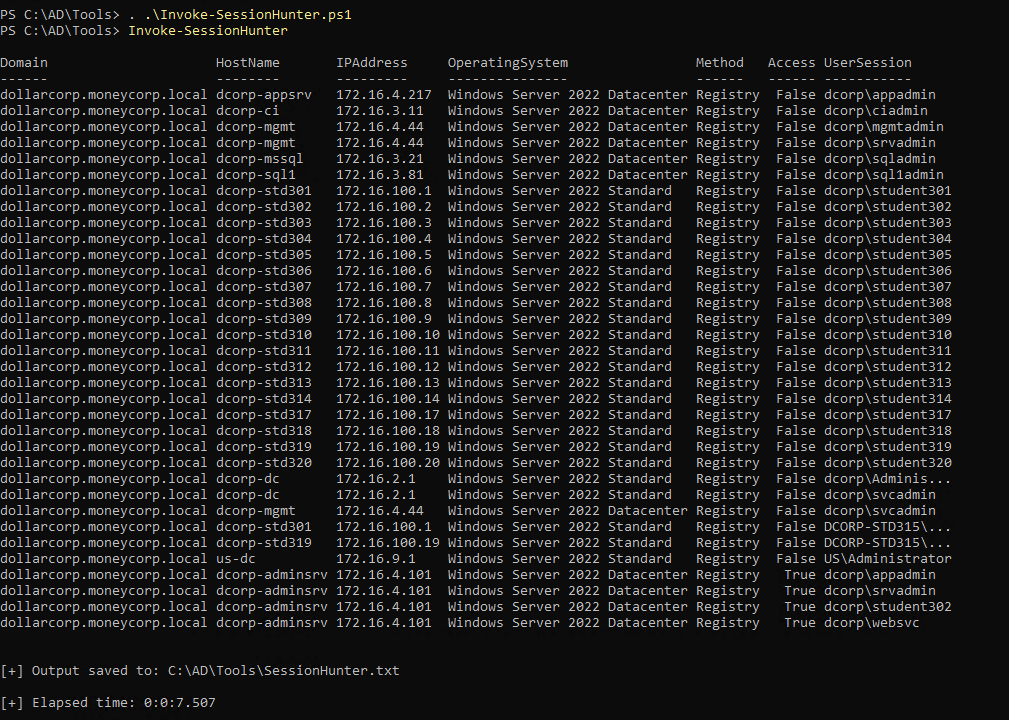
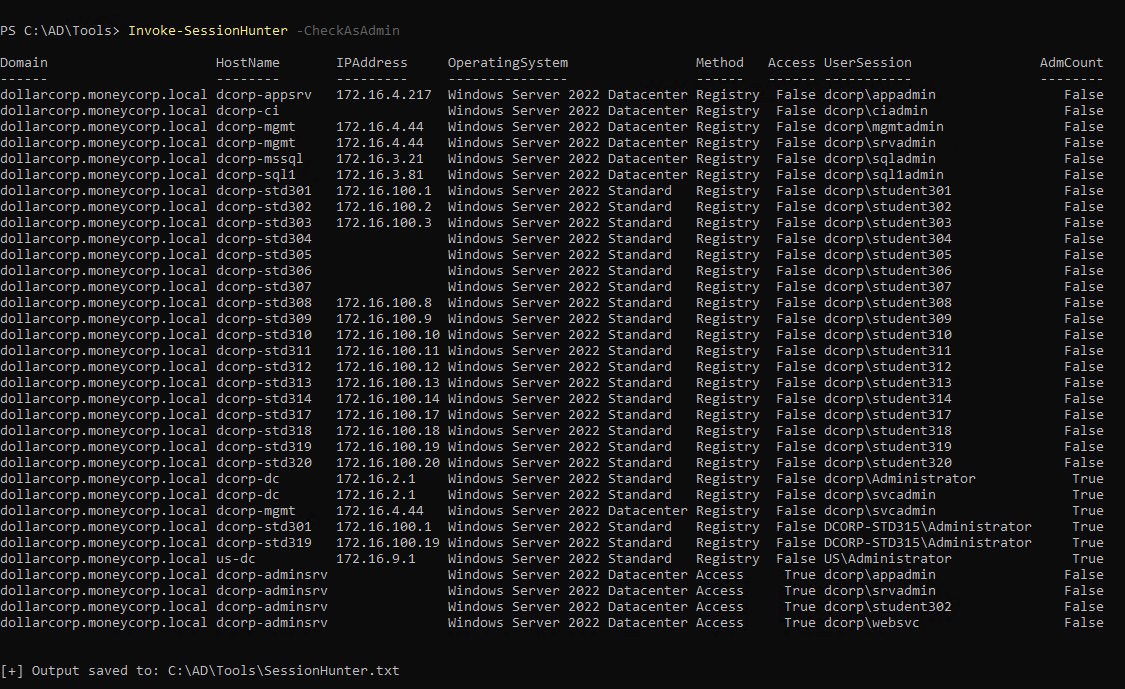
who has session on which computer
1
| Invoke-SessionHunter -CheckAsAdmin
|